Find the latest threat intelligences direct from AhnLab’s security experts
You can learn about the major security threats to the latest technical trends from AhnLab’s Tech Report. The Evolution of Magniber Ransomware. This analysis report will examine the recent malicious activities of Magniber ransomware from changes in exploited vulnerability to shellcode.
Threat Analysis_Operation Shadow Force
Operation Shadow Force
This analysis report will examine Operation Shadow Force that had been hidden behind legitimate certificates for the last seven years.
DownLoadThreat Analysis
Five Malicious Sextortion Apps
This analysis report will examine the top five malicious applications being used for sextortion scams.
DownLoad
Issue Report
Ahnlab Anti-ransomware Tool (beta)
The Evolution of Magniber Ransomware This analysis report will examine the recent malicious activities of Magniber ransomware from changes in exploited vulnerability to shellcode. DownLoad | |
Sour Lemon Duck: PowerShell Malware Exploiting SMB Vulnerability This analysis report presents the kill-chain, primary functions, and internal proliferation methods of Lemon Duck in full detail. DownLoad | |
Operation Kabar Cobra: Tenacious cyber-espionage by Kimsuky This report describes the latest attacks by Kimsuky Group including main methods, and changes in their purpose and targets. DownLoad | |
Full Discloser of Andariel, a Subgroup of Lazarus Threat Group This report describes the several cyberattacks by Andariel Threat Group including main methods, and changes in their purpose and targets DownLoad | |
Ghosts Dwelling in the USB Memory This analysis report will examine the the malware that has been dwelling in the USB memory during the last decade. DownLoad | |
Detailed Analysis of Red Eyes Hacking Group This report takes a closer look at the main activities of Red Eyes and another group that may be affiliated with it. DownLoad | |
Analysis Report on Attacks Targeting South Korea This report shows attacks targeting South Korea; attack method and hacking groups. DownLoad | |
Targeted Attacks on Defense Industry This report presents analysis of attacks on defense industry which can be serious concerns to national security. DownLoad |
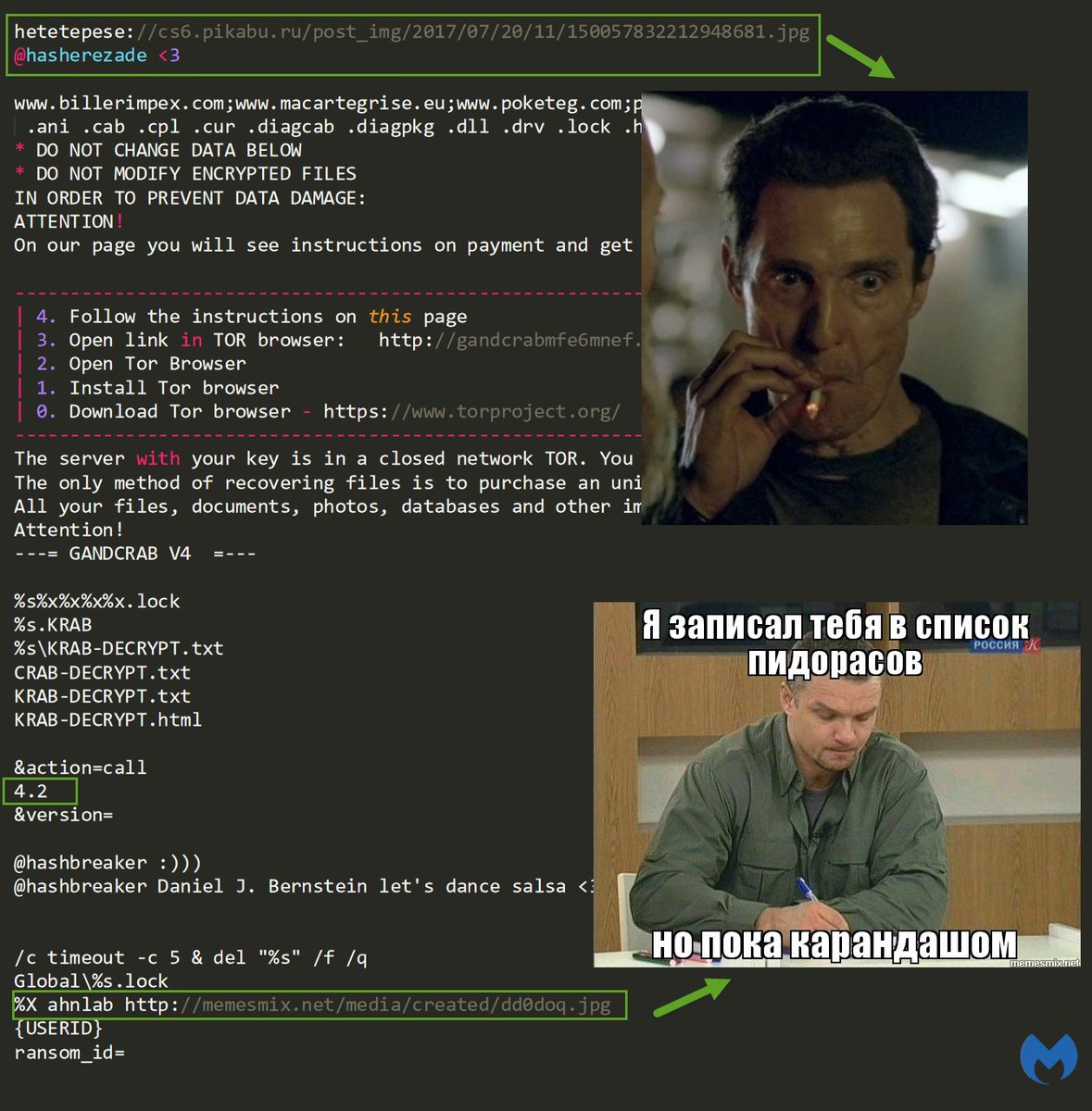
Most ransomware infect users’ computer by leading them to open compromised email attachments or visit malicious websites. WannaCryptor leveraged the Windows vulnerability (MS17-010, SMB Remote Code Execution Vulnerability) a. Ransomware indiscriminately. This newsletter introduces the latest ransomware trends and best practices for ransomware response using the AhnLab MDS (Malware Defense System). Today, ransomware is propagating under various names based on attack method and specific actions such as Teslacyrpt, Cryptowall and Teerac. Ransomware is a type of. AhnLab ASEC Analysis Team has been monitoring BlueCrab(=Sodinokibi) ransomware in form of Javascript distributed via phishing download page. The phishing download page is masquerading as the one to download utilities, and appears on the top of Google search results as Figure 1.
Overview
AhnLab EDR is an endpoint detection and response solution that provides actionable insights and holistic visibility for enhanced response.
AhnLab EDR is an Endpoint Detection and Response (EDR) solution that continuously monitors endpoints for comprehensive threat detection, analysis, and response.
Ahnlab Ransomware
New and unknown malware, including ransomware, and malware variants are intensifying at an alarming pace - but organizations do not have adequate response measures in place and rely on traditional endpoint security measures.
Ahnlab Malware
Ahnlab Anti-ransomware Tool
To mitigate the risks and strengthen your resiliency in security incidents, EDR technology is necessary. AhnLab EDR provides a total process of information detection, analysis, response, and prediction at endpoints. The response process enables holistic visibility into threats with continuous monitoring and recording of every activity in endpoints, analyzing the flow and enabling stronger response.
- Resources
- [White Paper] A Simple Guide to Understanding EDRDownload >
